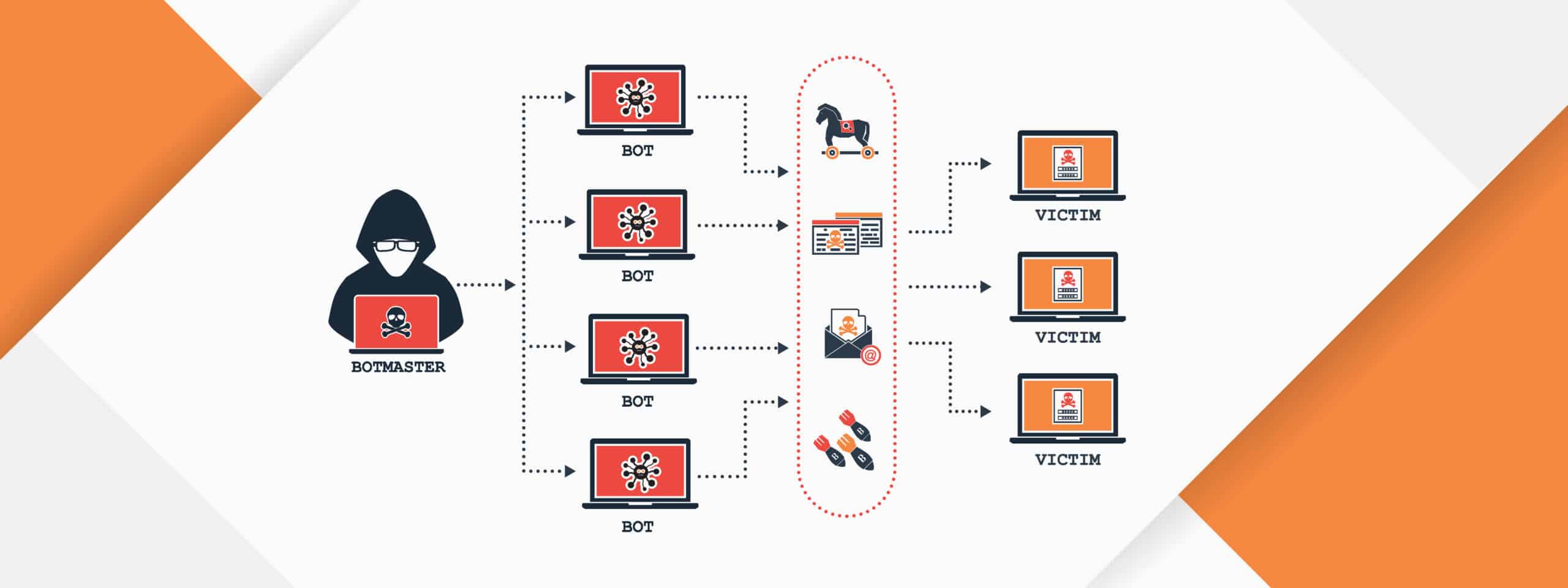
A botnet is a network of compromised computers or devices that are controlled remotely by an attacker, often referred to as a “botmaster” or “bot herder.” These devices, known as “bots” or “zombies,” can be used to carry out various malicious activities without the knowledge of their owners. Here’s a detailed overview of botnets, the dangers they pose, and how they can be recognized:
What is a Botnet?
- Compromised Devices: Botnets consist of a large number of infected devices, which can include personal computers, servers, Internet of Things (IoT) devices, and mobile phones. These devices are typically infected through malware, phishing, or exploiting vulnerabilities.
- Remote Control: The botmaster controls the botnet using command-and-control (C&C) servers, issuing commands to the bots to execute various tasks, such as launching attacks, sending spam, or stealing data.
Dangers Posed by Botnets:
- Distributed Denial of Service (DDoS) Attacks:
- Botnets can be used to perform DDoS attacks, overwhelming a target server, service, or network with massive amounts of traffic, rendering it unavailable to legitimate users.
- Spam Campaigns:
- Compromised devices can be used to send out large volumes of spam emails, often used for phishing attempts, distributing malware, or promoting scams.
- Data Theft:
- Botnets can be utilized to steal sensitive information, such as login credentials, financial data, and personal information, leading to identity theft and financial loss.
- Cryptojacking:
- Some botnets are used to hijack the processing power of infected devices to mine cryptocurrencies without the owner’s consent.
- Malware Distribution:
- Botnets can facilitate the distribution of additional malware, including ransomware, further compromising the security of infected devices.
- IoT Device Exploitation:
- With the rise of IoT devices, botnets can exploit poorly secured devices (e.g., smart cameras, routers) to create large networks of bots, often called “IoT botnets.”
- Evasion and Persistence:
- Botnets often employ various techniques to evade detection and maintain control over infected devices, making them difficult to eradicate.
How to Recognize a Botnet Infection:
- Unusual Network Activity:
- Monitoring network traffic can reveal abnormal patterns, such as excessive outgoing connections or large volumes of traffic during unusual hours.
- Performance Degradation:
- Infected devices may exhibit performance issues, such as slowdowns, freezing, or unresponsive behavior due to the extra load caused by botnet activity.
- Unexpected Software Installation:
- Users may notice unfamiliar applications or processes running on their devices that they did not intentionally install.
- Increased Bandwidth Usage:
- An unexplained increase in internet usage or data consumption could indicate that a device is part of a botnet.
- Frequent Crashes or Reboots:
- Devices that crash or reboot frequently may be experiencing issues related to botnet malware.
- Presence of Malware:
- Running antivirus or anti-malware scans can help identify and remove malware associated with botnet infections.
- Unusual Behavior:
- Devices may send or receive unexpected messages, display pop-up ads, or redirect users to unknown websites, indicating potential botnet activity.
- Suspicious Connections:
- Users can check active connections and identify suspicious IP addresses or domains that may be communicating with the botnet’s C&C servers.
Preventive Measures:
- Regular Updates: Keep operating systems, software, and firmware updated to protect against known vulnerabilities that botnets exploit.
- Use Strong Passwords: Implement strong, unique passwords for devices and accounts, and change default passwords on IoT devices to prevent unauthorized access.
- Network Security: Use firewalls, intrusion detection systems, and security software to monitor and protect against botnet activities.
- Educate Users: Provide training and awareness programs to help users recognize phishing attempts and avoid clicking on suspicious links or downloading unknown attachments.
- Device Security: Implement security measures on IoT devices, including disabling unnecessary features and regularly changing passwords.
- Regular Scans: Conduct periodic security scans to identify and remove malware infections from devices.
Summary
A botnet is a network of compromised devices controlled by an attacker, posing significant risks, including DDoS attacks, spam campaigns, data theft, cryptojacking, and more. Recognizing botnet infections involves monitoring for unusual network activity, performance issues, and unexpected software installations. Preventive measures include regular updates, strong password management, network security, user education, and routine malware scans to protect against botnets and their associated dangers.