Despite the availability of more secure alternatives, such as HTTPS (Hypertext Transfer Protocol Secure), HTTP (Hypertext Transfer...
Abbreviations
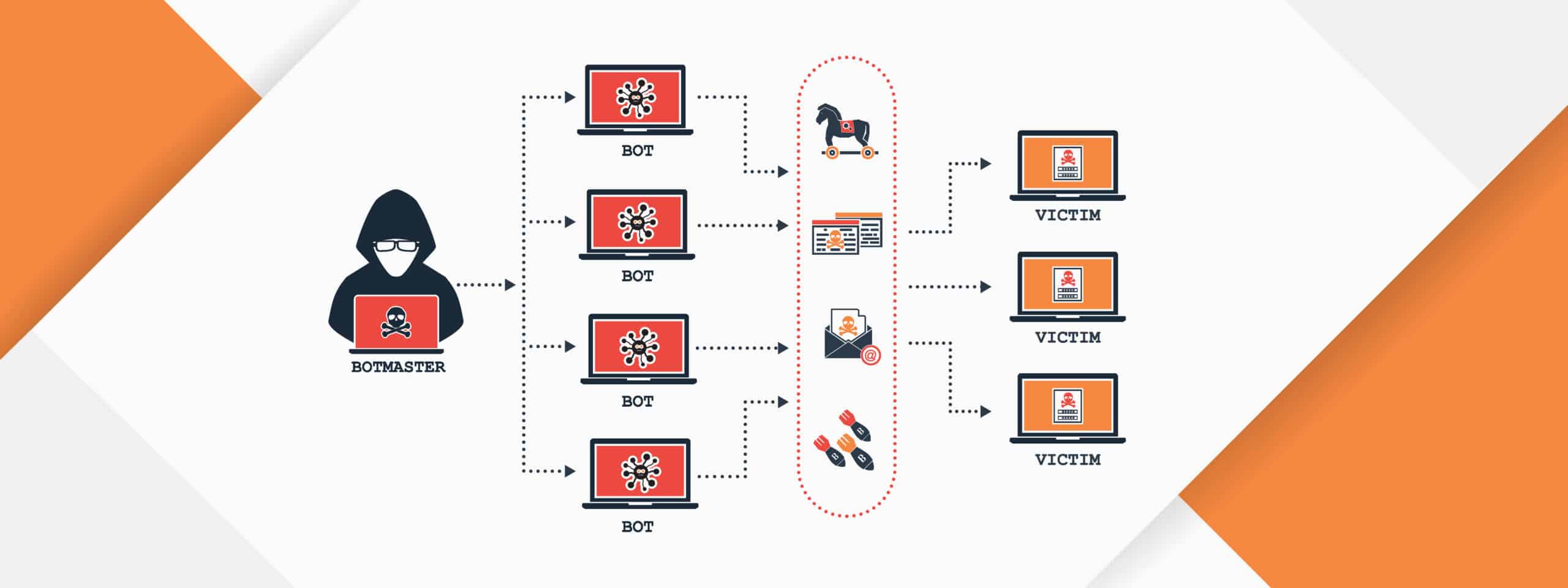
A botnet is a network of compromised computers or devices that are controlled remotely by an attacker,...
Network congestion occurs when the demand for network resources exceeds the available capacity, leading to a slowdown...
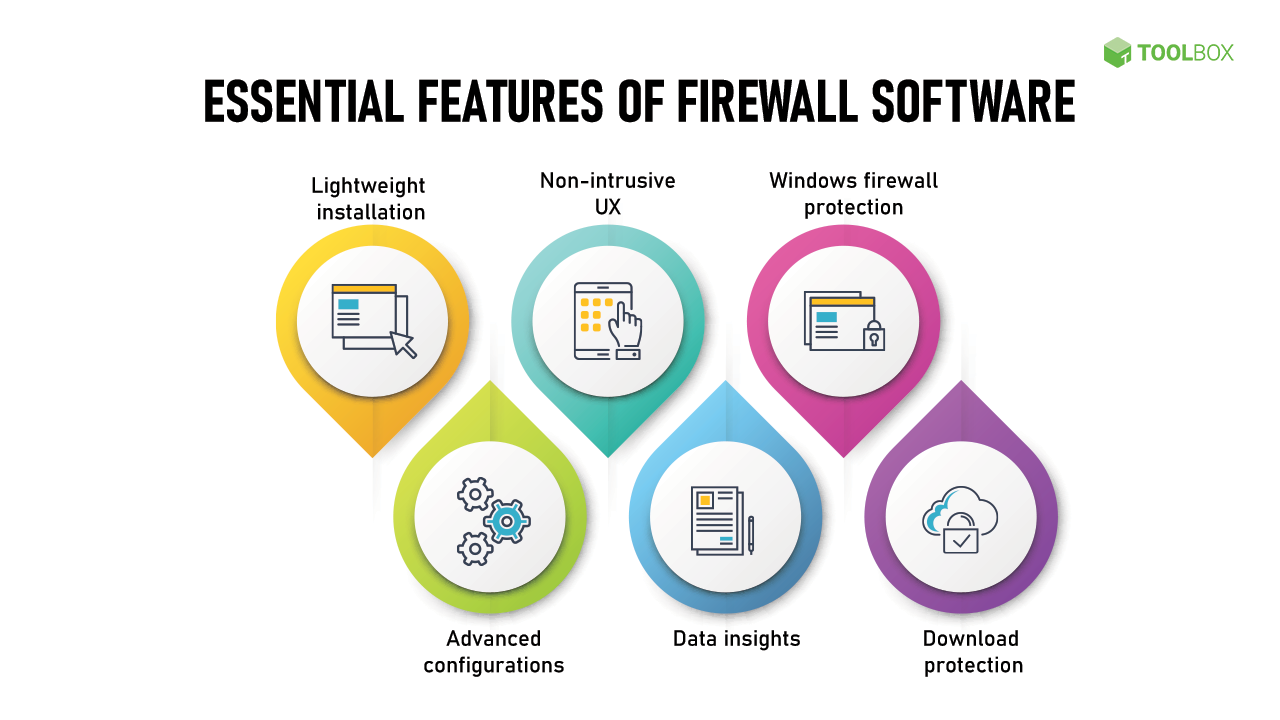
A good firewall is essential for maintaining the security of a network by monitoring and controlling incoming...
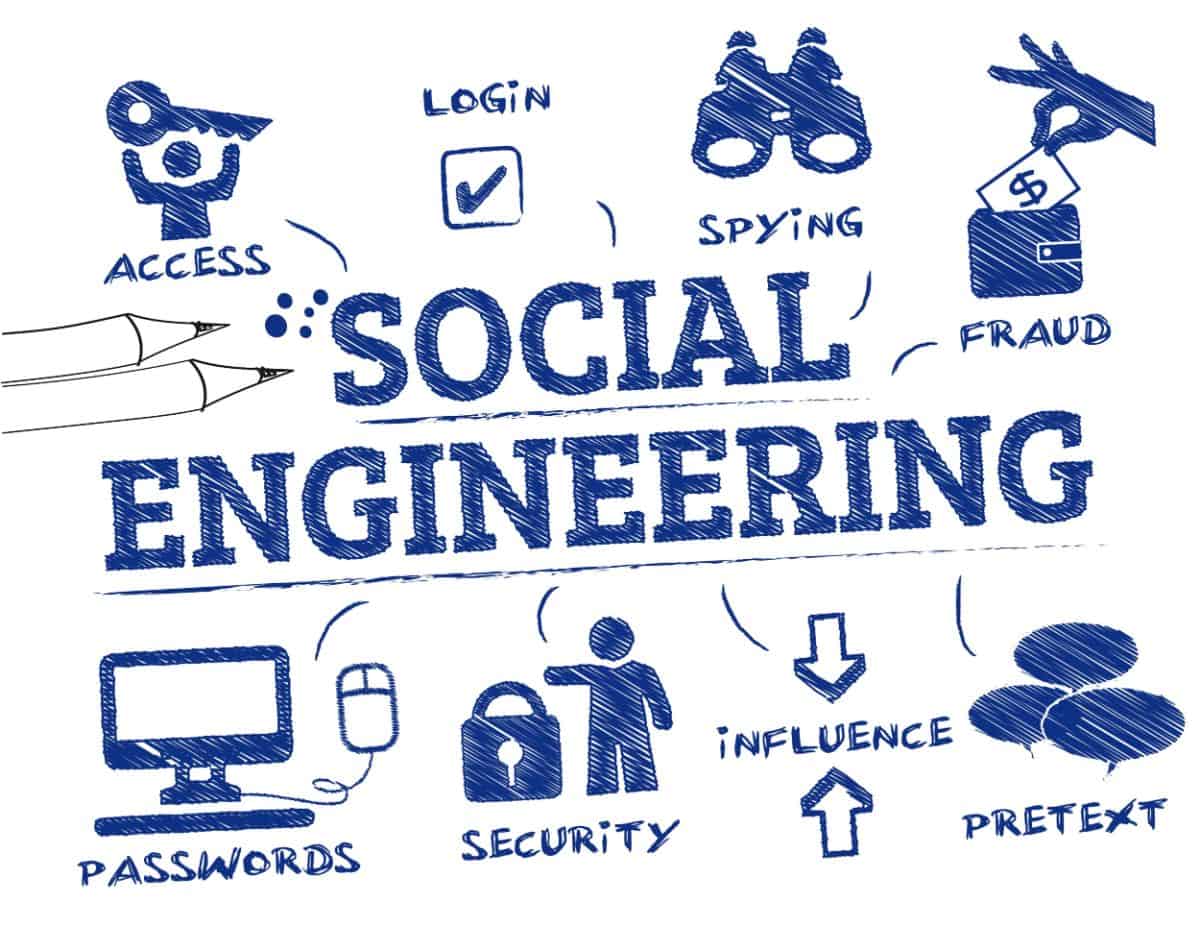
Social engineering is a manipulation technique that exploits human psychology rather than technical vulnerabilities to gain access...
VGA (Video Graphics Array) is a display standard that was introduced by IBM in 1987. It defines...
SSD (Solid State Drive) is a type of non-volatile storage device that uses flash memory to store...
SATA (Serial Advanced Technology Attachment) is an interface used to connect storage devices like hard drives (HDDs),...
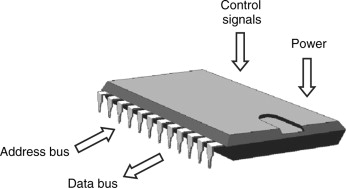
ROM (Read-Only Memory) is a type of non-volatile memory that stores data permanently. Unlike RAM, which loses...
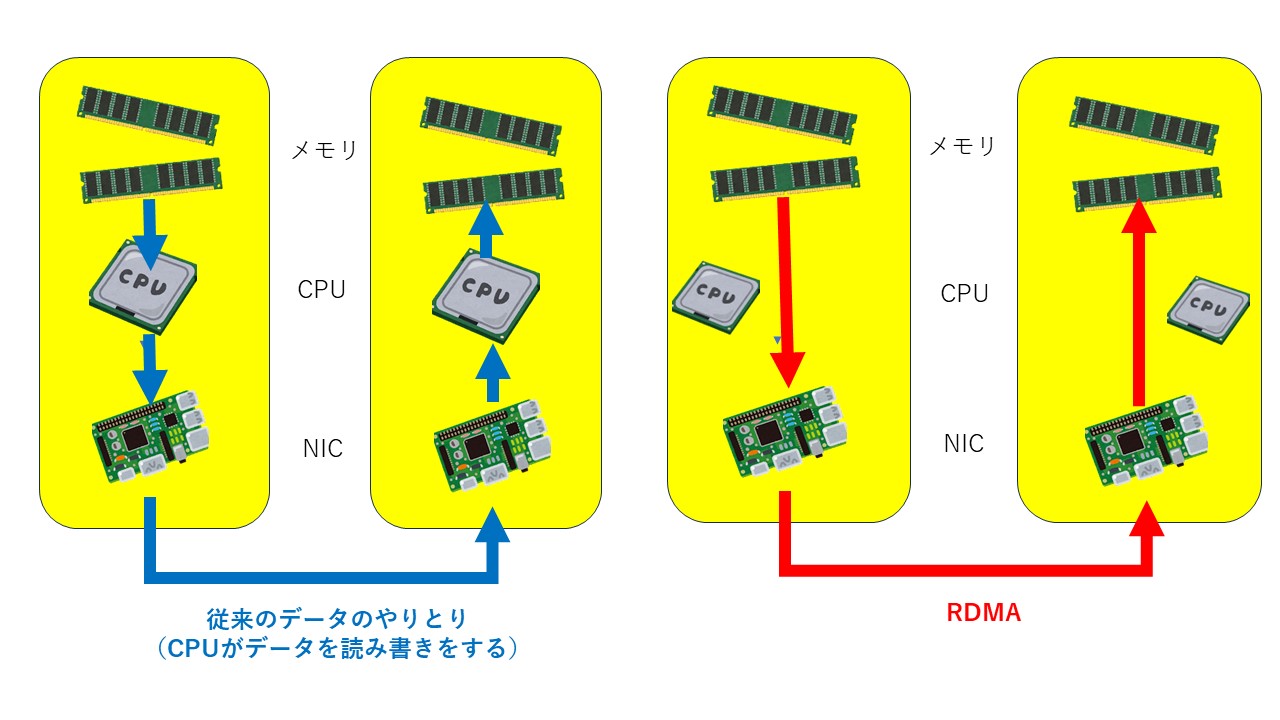
RDMA (Remote Direct Memory Access) is a technology that allows direct memory access from the memory of...